Workspace Monitoring and QA Solutions
Traditional, external threat mitigation solutions fail to protect against (or even address) the internal, insider threat data extraction (ie: cell phone audio/video recording, manual transcriptions, resource impersonation, location spoofing) and productivity losses.
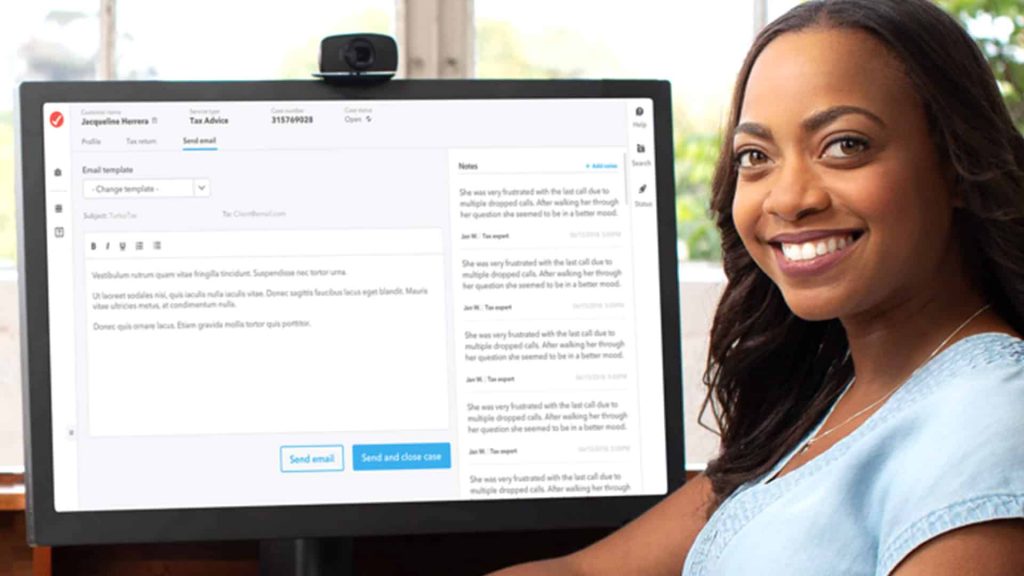
Standard QA processes spend hours of manual labor to find, score and coach on customer interactions. Even with all the hours put in over 95% of interactions are never scored or reviewed.
We solve these issues through our:
- Exclusive webcam workspace video surveillance
- Facial/object detection & identity verification
- Proprietary risk/productivity assessment
- Automated QA process that scores 100% of customer interactions
- Tailored coaching for agents and managers
- & more!
Solutions
Workspace Monitoring
Monitor compliance of compliant environment through identity verification, threat detection and automated flagging of risks to workspace environment.
Quality Assurance
Leverage automated Quality Assurance to accurately evaluate, score, rank and provide feedback to employees on 100% of customer interactions.
Documentation
Ensure every customer interaction is documented directly into your CRM notes field without agents having to lift a finger.

